Yes, if File Tracing and File Shadowing have been activated you can search the available shadowed files for credit card / social security or any other format specific data. Below are instructions how to do this search under Windows using a free tool called FileSeek.
For the Endpoint Protector Linux based file servers we recommend to use the "grep" Unix command.
Download and install the application FileSeek (freeware):
http://www.binaryfortress.com/fileseek/FileSeek supports Windows XP, Vista (x86/x64), Windows 7 (x86/64), 2003, 2008.
Select the directory path that contains the shadowed files that Endpoint Protector created.
Search for regular Expressions (in this case 16 digit credit card number format):
\b(?:\d[ -]*?){16}\bSelect "Process Query as a Regular Expression" in FileSeek.
The FileSeek Settings Screen is shown below:
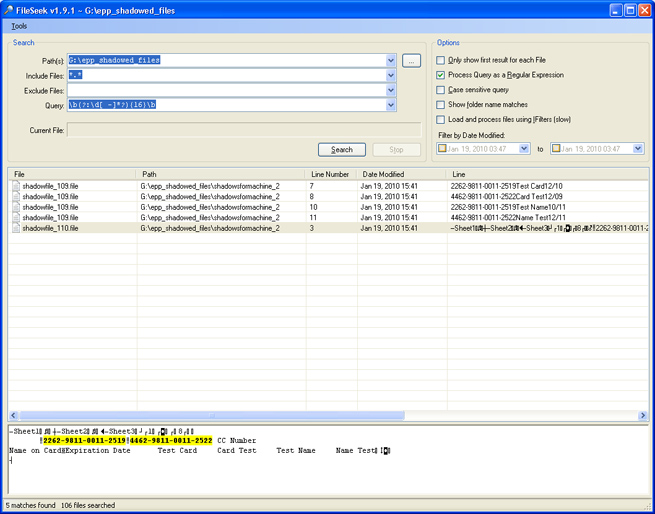
And start the search. If like in this case credit card information has been transferred you will see the results.
Additional useful information about Regular Expressions to search for other specific data format visit this website:
http://www.regular-expressions.info/creditcard.htmlThis also provides you information how to search for other data formats like Social Security Numbers etc.
If your search gives you a positive result you can find out from what computer the file containing the credit card number(s) have been transferred.
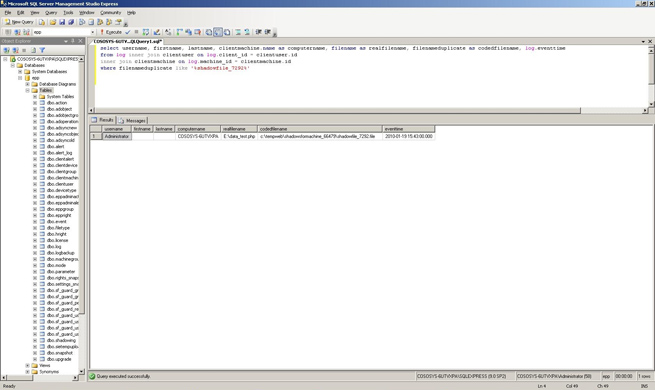
The file results in FileSeek will have this form: "shadowfile_aNUMBER.file" (the EPP shadow files format). To find out the actual name of the copied file, who copied it and when, you must run the following sql query in the SQL Studio Express console:
select username, firstname, lastname, clientmachine.name as computername, filename as realfilename, filenameduplicate as codedfilename, log.eventtime from log inner join clientuser on log.client_id = clientuser.id inner join clientmachine on log.machine_id = clientmachine.id
where filenameduplicate like '%shadowfile_aNUMBER%'